Barracuda threat spotlight: Inbox rules evade detection

Research conducted by Barracuda found that 75% of the companies that it surveyed worldwide had at least one email security breach in 2022.
According to the company, email-borne attacks have a high success rate and they provide a common entry point for many other cyberattacks. In the first half of 2023 alone, the number of email-based phishing attacks surged 464% in comparison to 2022.
According to Barracuda, attackers can use inbox rules to hide in plain sight while moving information out of the network via an email inbox, ensuring victims do not see security warnings, or deleting messages from the senior executive they are pretending to be in an attempt to extract money.
‘Bad actors’ using emails to evade detection
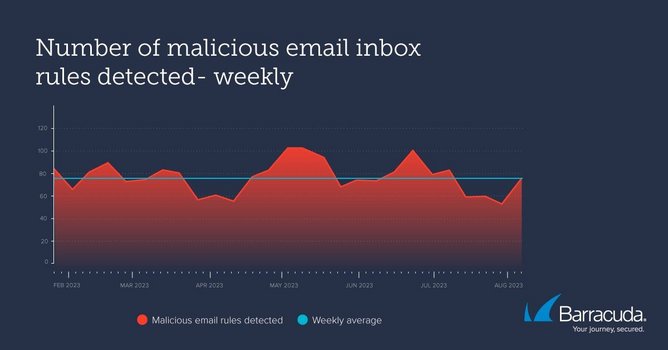
Barracuda’s detection numbers suggest that attackers continue to access networks and that immediate action is required to get them out.
Email detection has advanced over the years, with the use of machine learning making it easier to spot suspicious rule creation, but Barracuda states that attackers continue to infiltrate with success. The company is clear that these attack methods pose a serious threat to the integrity of an organisation’s data and assets.
Barracuda also highlights that these cyberattacks range from basic phishing and malicious links or attachments, to sophisticated social engineering techniques such as business email compromise (BEC), conversation hijacking and account takeover. Some of the most advanced types are associated with malicious email rules.
In addition, Barracuda says that attackers may use email rules to steal information or money and delay detection as a result. It says that attackers might set a rule to forward to an external address all emails containing sensitive and key words such as “payment,” “invoice,” or “confidential.”
Attackers might also use email rules to hide specific inbound emails by moving such messages to rarely used folders, marking emails as read, or deleting them. They could do this to hide security alerts, command-and-control communications, responses to internal spear-phishing emails sent from the compromised account, or to hide their tracks from the account owner who is likely using the account at the same time, unaware of intrusion.
If the malicious rule is not spotted, Barracuda says that it stays operational even if the victim's password is changed, if they turn on multi-factor authentication (MFA), or their computer is completely rebuilt. As long as the rule stays in place, it remains effective.
Even though suspicious email rules can be a good indication of an attack, looking at them in isolation may not provide a strong enough signal that an account has been compromised. Barracuda says that defences must employ multiple signals to reduce noise and alert the security team.
Ultimately, the dynamic and evolving nature of cyberattacks, including the use of sophisticated tactics by attackers, with cybercriminals constantly improving tactics to exploit vulnerabilities. It stresses the need for a multi-faceted approach to detection and defence.
Barracuda explains that, because inbox rule creation is a post-compromise technique, the most effective protection is prevention - stopping attackers from being able to compromise the account in the first place. But effective detection and incident response measures are also necessary to identify breached accounts and mitigate impact.
Manager of Email Protection Product Management at Barracuda, Prebh Dev Singh, says: “The abuse of email inbox rules is a brilliantly effective attack tactic that provides stealth and is easy to implement once an attacker has compromised an account. Even though email detection has advanced over the years, and the use of machine learning has made it easier to spot suspicious rule creation – our detection numbers show that attackers continue to implement this technique with success.
“Malicious rule creation poses a serious threat to the integrity of an organisation’s data and assets. Because it is a post-compromise technique, it’s a sign that attackers are already in your network. Immediate action is required to get them out.”
******
For more insights into the world of Cyber - check out the latest edition of Cyber Magazine and be sure to follow us on LinkedIn & Twitter.
Other magazines that may be of interest - Technology Magazine | AI Magazine.
Please also check out our upcoming event - Cloud and 5G LIVE on October 11 and 12 2023.
******
BizClik is a global provider of B2B digital media platforms that cover Executive Communities for CEOs, CFOs, CMOs, Sustainability leaders, Procurement & Supply Chain leaders, Technology & AI leaders, Cyber leaders, FinTech & InsurTech leaders as well as covering industries such as Manufacturing, Mining, Energy, EV, Construction, Healthcare and Food.
BizClik – based in London, Dubai, and New York – offers services such as content creation, advertising & sponsorship solutions, webinars & events.






