Checkmarx uncover attack impersonating GitHub Dependabot

New research reveals how a threat actor started compromising hundreds of private and public GitHub repositories and making them appear to be contributed by Dependabot - GitHub’s automated dependency management tool.
The research team at Checkmarx discovered that cyber attackers used a technique to fabricate commit messages to trick developers into thinking it was contributed by the real Dependabot, to carry out malicious activity.
Amongst the findings, the research shows how victims had their GitHub personal access token stolen, which was used by the attackers to contribute malicious code contributions. Hacks like this stress how cyber criminals continue to exploit digital systems and so resilience is a must.
Hacking Dependabot: Malicious code tricking customers
Dependabot is GitHub’s free automated dependency management tool for software projects. It continuously monitors a project's dependencies (like libraries and packages) for security vulnerabilities and outdated versions. When it detects issues, it automatically generates pull requests with updates, helping developers keep their software secure and up to date.
The cyber attackers were able to access accounts using compromised personal access tokens (PATs). These were most likely exfiltrated silently from the victim’s development environment – not requiring 2FA.
Malicious code is then injected into repositories designed not only to exfiltrate project secrets, but also to modify JavaScript files with a web-form password-stealer malware. This ultimately puts end-users at risk of having their passwords stolen.
The code exfiltrates the GitHub project’s defined secrets to a malicious C2 server and modifies any existing JavaScript files in the attacked project with a web-form password-stealer malware code effecting any end-user submitting its password in a web form.
According to Checkmarx, it is currently unclear how the victims’ PATs were stolen and speculate that it may be due to a malicious open source package installed on their PC.
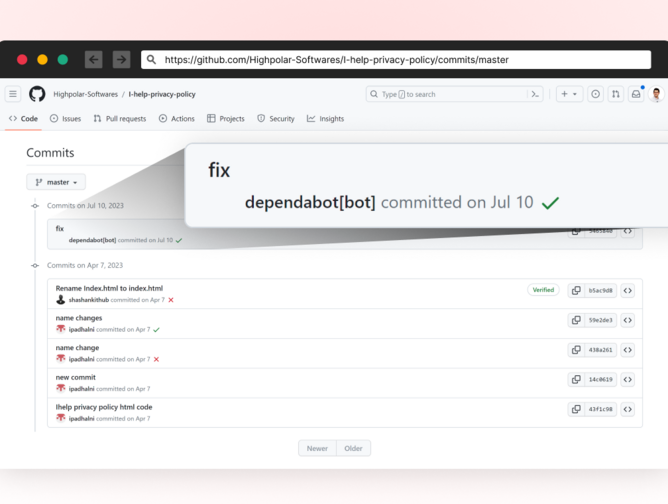
In July 2023, threat actors started compromising hundreds of private and public GitHub repositories. Most victims are Indonesian user accounts. The attackers used a technique to fake commit messages (read more about how it’s done here) to trick developers thinking this was contributed by the real Dependabot.
At first it was unclear to us how the attacker’s got access to those accounts, so Checkmarx spoke with some of the victims by notifying them of the breach and asking for help understanding the full picture.
This revealed that the attackers accessed the accounts using compromised PATs (Personal Access Token), most likely exfiltrated silently from the victim’s development environment. Checkmarx states that it teaches users to be careful about where they get their code, even from trusted places, as large platforms can also have problems.
This is the first incident that Checkmarx has witnessed a threat actor using fake git commits to disguise activity, knowing that many developers do not check the actual changes of Dependabot when they see it.
The attacker's Tactics, Techniques, and Procedures (TTPs) involve the use of fake commits, stealing user credentials, and impersonating Dependabot to avoid detection demonstrate, according to Checkmarx, that supply chain attacks are getting more sophisticated, as attackers realise it does not take much to move silently.
******
For more insights into the world of Cyber - check out the latest edition of Cyber Magazine and be sure to follow us on LinkedIn & Twitter.
Other magazines that may be of interest - Technology Magazine | AI Magazine.
Please also check out our upcoming event - Cloud and 5G LIVE on October 11 and 12 2023.
******
BizClik is a global provider of B2B digital media platforms that cover Executive Communities for CEOs, CFOs, CMOs, Sustainability leaders, Procurement & Supply Chain leaders, Technology & AI leaders, Cyber leaders, FinTech & InsurTech leaders as well as covering industries such as Manufacturing, Mining, Energy, EV, Construction, Healthcare and Food.
BizClik – based in London, Dubai, and New York – offers services such as content creation, advertising & sponsorship solutions, webinars & events.






