Emotet Malware 2023 Resurgence

Active since 2014, Emotet is a sophisticated modular banking trojan that is normally used to distribute other types of malware.
Despite facing law-enforcement activity in 2021, Emotet has resurged in 2022 and continues to deploy additional types of sophisticated malware, including ransomware, post-compromise. During 2022 SecurityHQ saw a wave of activity, whereby Emotet was seemingly the malware of choice to deliver ransomware payloads.
What is interesting about Emotet is that it contains multiple features. Emotet is designed to steal credentials, harvest email addresses, distribute spam, enable lateral movement, and download other types of malware.
How Does Emotet Impact Business?
Emotet presents a persistent threat to organizations worldwide. The operators of the malware frequently take breaks before returning with new threat campaigns deploying new tactics.
Emotet is also known for the following:
- It catches organisations off guard, as the operators of the malware often pause campaigns for significant amounts of time, then return with a new tactic.
- Emotet not only resurged in 2022, but continue to deploy sophisticated malware, including ransomware post-compromise.
- Ransomware groups, (specifically Conti, Quantum Locker and ALPHV) were observed using Emotet to distribute their Ransomware payloads.
In 2022 SecurityHQ observed over 266 incidents, that were handled and remediated globally. SecurityHQ also released 3 Threat Intelligence Advisories, published internally to spread awareness of the malwares growth.
From documenting the malware, it is clear just how active Emotet has been throughout 2022. This graph showcases data taken from SecurityHQ’s global Security Operation Centres.
The red line highlights incidents that were worked, from a cyber defence perspective. You can see the common trend with Emotet, whereby the group comes up with a campaign, they then take a break, and come back with a vengeance. Emotet do not operate all year round, they do a campaign, then go quiet again, and so on. Which is why you can see this up and down trend.
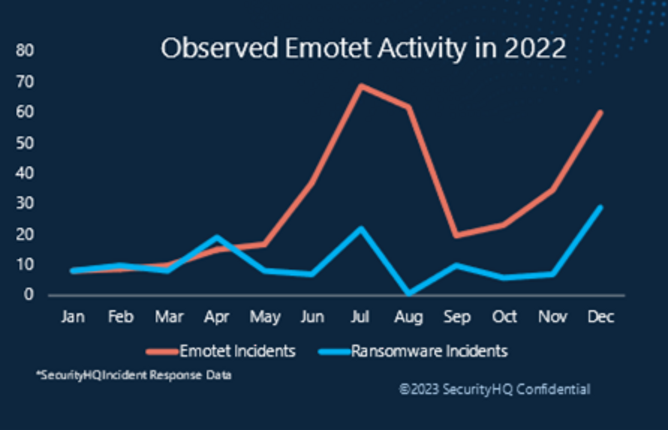
But now, take the blue line. If we, SecurityHQ analysts, link the fact that Emotet was used by ransomware payloads to get initial access, you will notice an interesting trend, where the blue line denotes ransomware incidents that we saw over the year. Set alongside the red Emotet activity over the year, what we see is that wherever Emotet activity spiked in our data, we also observed a spike of ransomware related incidents. You can see that around July/ August time, and the end of the year around November/December time, with both lines showing a clear upwards trend.
This shows that as there as a trend of Emotet related incidents, so there was a trend in Ransomware attacks.
Recommendations to Avoid Being Impacted by Emotet Campaigns in 2023
- Vulnerability Management as a Service (VMaaS)- Vulnerability Management can be used to view and act on all vulnerabilities across all your digital platforms, including internet, applications, systems, cloud and hardware. Identify your weak points, monitor your online identity, verify issues and remediate in rapid time.
- Penetration Testing – Ensure that your cyber security team, or MSSP, routinely conducts External Penetration Testing, Internal Penetration Testing, Web Application Security Testing, Mobile Application Security Assessment (Android, Apple & Windows), Wireless Network Security Assessment and Cloud Penetration Testing in order to highlight the vulnerabilities in your systems.
- User Behaviour Analytics (UBA) – User Behaviour Analytics is useful to observe what constitutes normal behaviour, and to detect abnormal activity within a given environment. If an unusual action is made on a device on a given network, such as an employee login late at night, inconsistent remote access, or an unusually high number of downloads, the action and user is given a risk score based on their activity, patterns and time.
- Phishing Attack Simulation - The two main objectives of Phishing Attack Simulation are to gauge the level of employee awareness and analyse the level of training required for employees to identify phishing attacks, and to validate effectiveness of preventative controls in place, to be able to detect phishing attacks.
- Training - Ensure that employees are educated so that they understand how to spot a phishing attack, and therefore reduce their risk of clicking on malicious links and assets. Watch this video on ‘Tips to Education and Protect Your Staff on Security Threats.’
For more on Emotet, a review of similar malware, and a prediction on the emerging and resurging threats to come out of 2023, watch this webinar on ‘Global Threat Landscape 2023 Forecast’.






